Below is a detailed breakdown of the rumored affiliations of the “Black Mirror” hacker group, including the specific sources and web links that reported on the Su-35 document leak.
Primary Suspected Affiliation: Pro-Ukrainian Hacktivists
This is the consensus view among cybersecurity researchers and intelligence analysts. The evidence is circumstantial but strong, based on the group’s actions, timing, and statements.
Sources and Evidence:
- The Leak Announcement on Telegram:
· The “Black Mirror” group itself announced the leak on its Telegram channel, a primary communication platform for such groups.
· Key Source: While the original channel may change or be taken down, their announcements were widely reported and screenshotted by cybersecurity monitors.
· Link to a Reporter’s Archive: Security researcher and journalist Dmitry Smilyanets often archives these posts. In a post about the leak, he highlighted their message which stated they leaked data “in support of Ukraine.”
· Dmitry Smilyanets’ Tweet: https://twitter.com/dsmilyanets/status/1772603212899127707 - Reporting by Cybersecurity News Outlets:
· The Record by Recorded Future: This reputable cybersecurity news site published a detailed article titled “Pro-Ukrainian hackers leak documents on Russian Su-35 fighter jet.”
· Key Points from the Article: It confirms the group leaked 30 GB of documents from the Russian United Aircraft Corporation (UAC) and the Ministry of Defense’s “RuBoard.” It explicitly labels “Black Mirror” as a “pro-Ukrainian hacker group.”
· Link: https://therecord.media/pro-ukrainian-hackers-leak-su-35-documents - Analysis by Threat Intelligence Firms:
· Cyberknow: A widely-followed threat intelligence platform on Twitter/X and LinkedIn, consistently tracks hacktivist groups. They have repeatedly classified “Black Mirror” as a pro-Ukrainian cyber collective.
· Key Source: Their analysis of the Su-35 leak, including details about the types of documents (technical manuals, diagrams) and the targeted entities.
· Cyberknow Post on the Leak: https://twitter.com/cyberknow20/status/1772571010972008865
Secondary, More Speculative Theory: Potential Ukrainian Intelligence Links
This theory suggests “Black Mirror” might have ties beyond simple hacktivism, possibly to Ukrainian state security services (SBU or GUR). This is not the mainstream view but is considered by analysts due to the high-value target.
Sources and Context:
- Statement from Russian Sources:
· The Russian state news agency TASS reported on the leak, quoting a law enforcement source who claimed, without providing evidence, that the hack was “carried out by Ukrainian special services.”
· Context: Russian authorities routinely blame Ukraine for cyber incidents, so this claim must be treated with caution. However, it shows that this theory exists in the public discourse.
· Link to TASS Article: https://tass.com/emergencies/1763199 (Note: This is the Russian state perspective). - Analyst Commentary:
· In its reporting, The Record (linked above) includes analysis from experts who note that while the group appears to be hacktivist, the sophistication and targeting align with goals that would be highly beneficial to Ukrainian military intelligence. The line between independent “patriotic” hacking and state-direction can be blurry.
Summary of Key Facts from the Leak (with Sources)
· Who was hacked? The “Black Mirror” group claimed to have breached the United Aircraft Corporation (UAC) and the Russian Ministry of Defense’s “RuBoard” system.
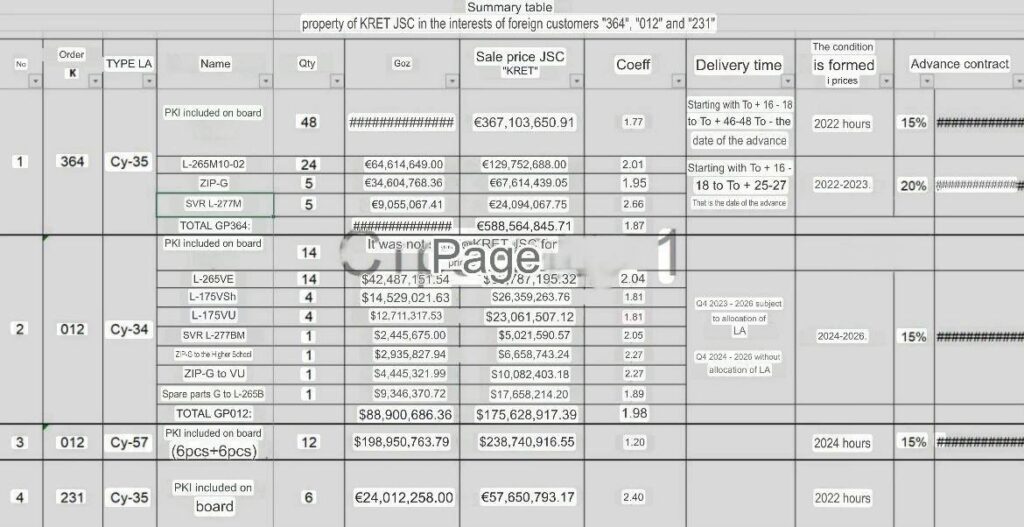
· What was leaked? Approximately 30 GB of documents related to the Sukhoi Su-35S fighter jet. This included technical manuals, diagrams, and other sensitive specifications.
· Where was it announced? On the group’s Telegram channel, which was then picked up by cybersecurity monitoring accounts and news outlets.
· What was the stated motive? The group’s messages framed the leak as an act “in support of Ukraine.”
Conclusion:
Based on available public sources, the “Black Mirror” group is overwhelmingly characterized as a pro-Ukrainian hacktivist collective. Their actions are ideologically aligned with Ukraine’s defense against the Russian invasion. The more speculative theory of direct state sponsorship, while occasionally raised by Russian sources and considered by analysts, lacks public, verifiable evidence and is not the consensus view within the cybersecurity community.

